Fireeye Cyber Threat Map
Ad Apply for Jobs in Cyber Security Companies. FIREEYE CYBER THREAT MAP.
 Fireeye Cyber Threat Threat Cyber
Fireeye Cyber Threat Threat Cyber
Real-Time Cyber Threat Map.

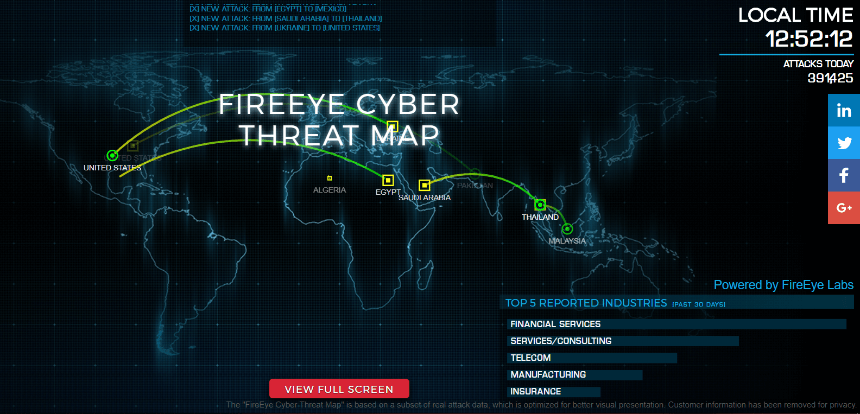
Fireeye cyber threat map. FireEye recently released a ThreatMap to visualize some of our Threat Intelligence Data. Use our interactive Cyber Threat Map which shows in real time the geolocation of cybercrime servers that are actively engaged in criminal activity such as credit card theft credential theft or malware distribution. Gain knowledge of attacks before they happen.
Are You Looking for a Job that Fits Your Qualifications as Cyber Security Expert. Live Cyber Attack Map. Ad Empowering threat analysts in their fight against advanced cyber adversaries.
The data represented in the map is malware communication to command and control C2 servers where the Attackers represent the location of the C2 servers and Targets represent customers. And anyone can access it via our free API. What is Norse attack map.
Ad Explore new cybersecurity trends technologies and approaches. FireEyes sinkhole and dynamically shared threat data indicate that the following crimeware variants were the most commonly detected in the high tech and IT industry. FireEye Cyber Threat Map.
0 attacks on this day. It only shows origin destination total number of attacks and some interesting stats about the previous 30 days such as top attacker countries and top most attacked industries. Identify threats to your assets outside your perimeter and across the deep and dark web.
DDoS Digital Attack Map. Recently we were attacked by a highly sophisticated threat actor one whose discipline operational security and techniques lead us to believe it was a state-sponsored attack. Together we can make networks devices and applications more secure.
A Threatening Threat Map. We witness the growing threat firsthand and we know that cyber threats are always evolving. Are You Looking for a Job that Fits Your Qualifications as Cyber Security Expert.
FireEye is on the front lines defending companies and critical infrastructure globally from cyber threats. Together we can make networks devices and applications more secure. Real-time visibility into global cyber attacks.
Visibility beyond your walls. Our team developed a custom Unity3D application that visualizes client provided JSON data feeds in a dramatic visual story. The FireEye Cyber Threat Map is the last map we recommend basically because this one doesnt bring a lot of features to the table.
Ad Explore new cybersecurity trends technologies and approaches. Conficker is a worm that spreads by exploiting a vulnerability on removable drives and network shares. FireEye developed this definition specifically to emphasize adversaries given.
FireEye Cyber Threat Map. Observations from the Front Lines of Threat. Search black markets social media and paste sites for signs of compromise.
FireEye defines cyber threat intelligence as evidence-based knowledge about adversaries their motives intents capabilities enabling environments and operations focused on an event series of events or trends and providing a decision advantage to the defender. One may also ask how does FireEye threat map work. Ad Empowering threat analysts in their fight against advanced cyber adversaries.
Ad Apply for Jobs in Cyber Security Companies. 90 LCD display visualizing realtime cyber attack data for FireEye Executive Briefing Center at their headquarters in Milipitas CA.
Fireeye Cyber Threat Map Mcyseka Maritime Cyber Security Knowledge Archive
 Receive Cyber Attack Alerts Fireeye
Receive Cyber Attack Alerts Fireeye
 Fireeye Cyber Threat Map On Vimeo
Fireeye Cyber Threat Map On Vimeo
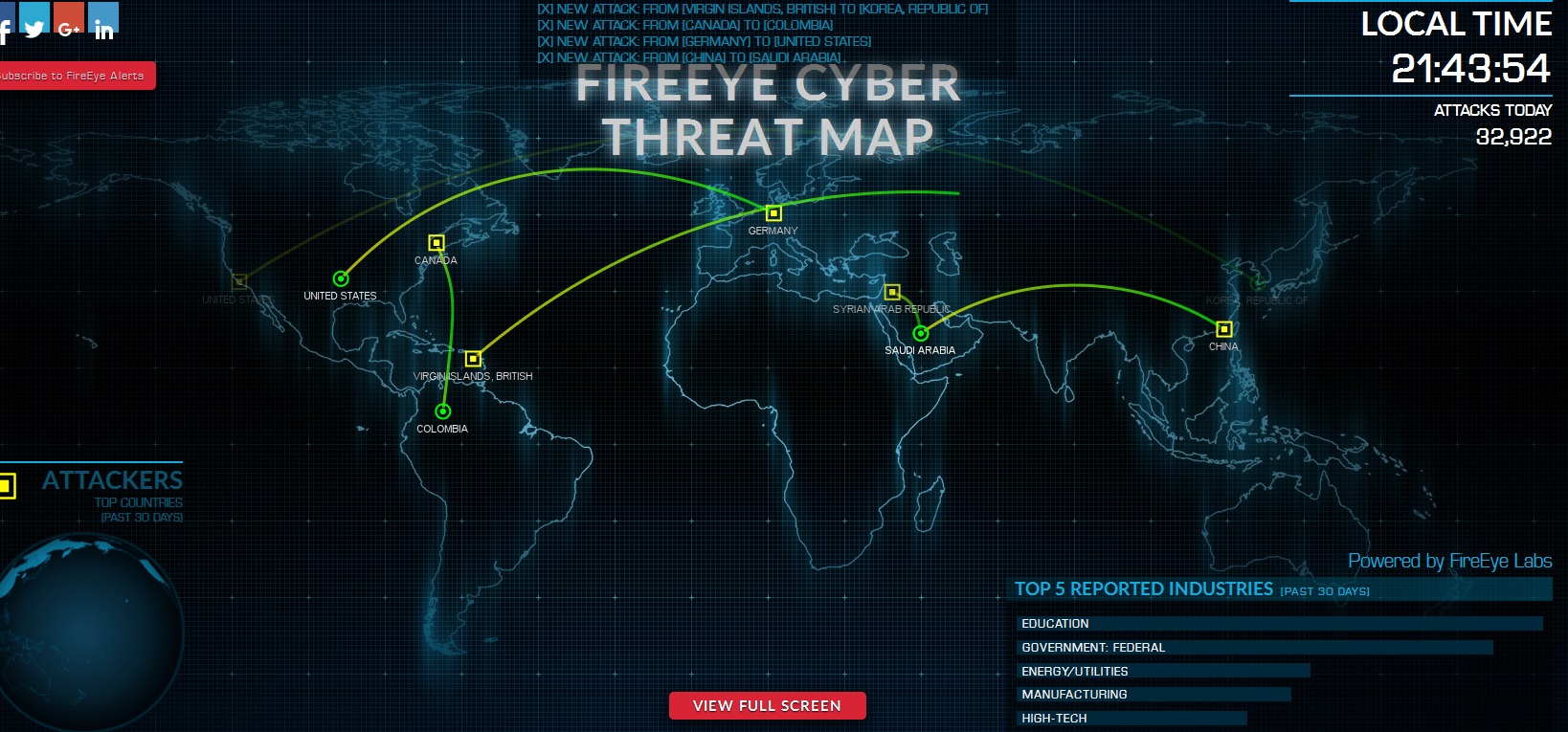 Top 7 Cyber Attack Maps Hacking News
Top 7 Cyber Attack Maps Hacking News
 Top 15 Live Cyber Attack Maps For Visualizing Digital Threat Incidents Norse Corp Com
Top 15 Live Cyber Attack Maps For Visualizing Digital Threat Incidents Norse Corp Com
 Fireeye Cyber Threat Map Visualization System Interface 11 Download Scientific Diagram
Fireeye Cyber Threat Map Visualization System Interface 11 Download Scientific Diagram
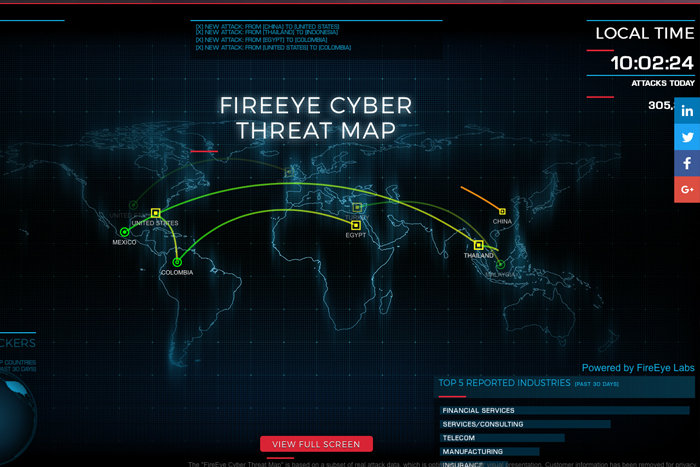 Fireeye Cyber Threat Map Fasrmetro
Fireeye Cyber Threat Map Fasrmetro
 Fireeye Cyber Threat Map Visualization System Interface 11 Download Scientific Diagram
Fireeye Cyber Threat Map Visualization System Interface 11 Download Scientific Diagram
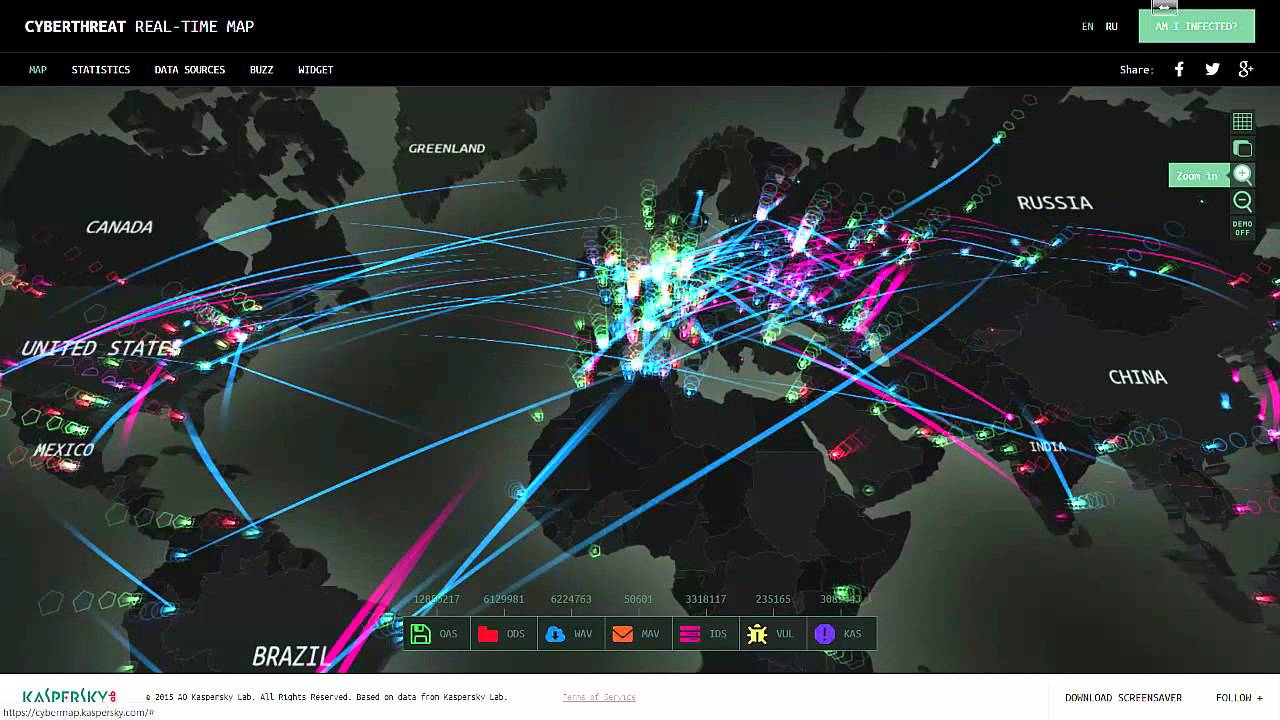 Cyber Computer Security Keamanan Sistem Informasi 1543978628 Video Cyber Threat Real Time Map
Cyber Computer Security Keamanan Sistem Informasi 1543978628 Video Cyber Threat Real Time Map
 Live Cyber Attacks Map It Nota
Live Cyber Attacks Map It Nota
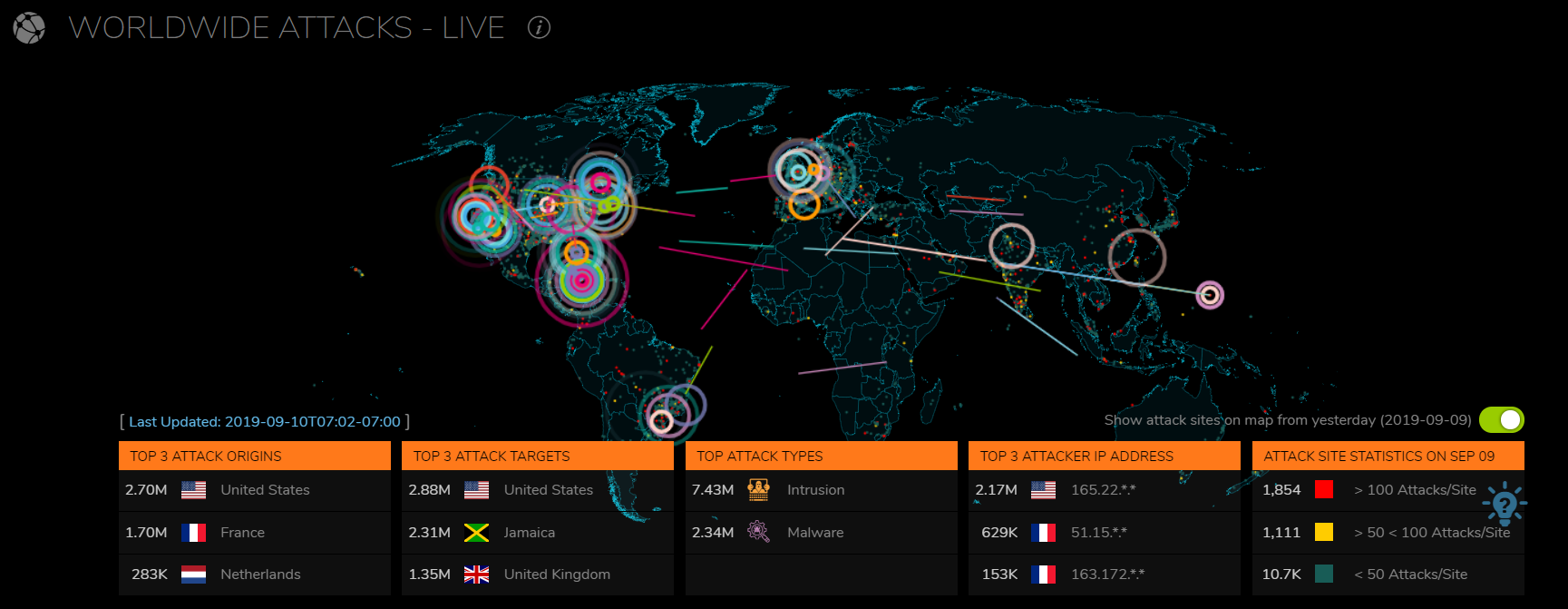


Comments
Post a Comment